Integrate your Cyber Security Tools into various SIEM, SOAR, XDR, Front Desk Tools and Tailor-Made Applications
Start building your Products with us at budget friendly rates in a span of 2 weeks.
Start building your Products with us at budget friendly rates in a span of 2 weeks.







Integrate your customized product in a span of 2 weeks.
Our on demand security delivery service is cutting edge.
Your personalized Security App development & Integrations at budget-friendly rates.
We develop cyber-security Integrated apps by reading the Events, Alarms, Detections, Incidents, IoTs, IoCs, Domains, Hashes, IPs, etc.. and develop custom dashboard to show the results and reports as per the Client’s requirement. In addition to that we create workflows, playbooks for the Integrated apps and provide dedicated support to the integrations. Digital Shadows, QRadar, and other security application development tools were utilised in-house. We automated change management procedures for comprehensive risk assessments and enhanced cyber hygiene and risk management by centralising and optimising firewall administration.



Provide your requirements and get your PoC done in a week.
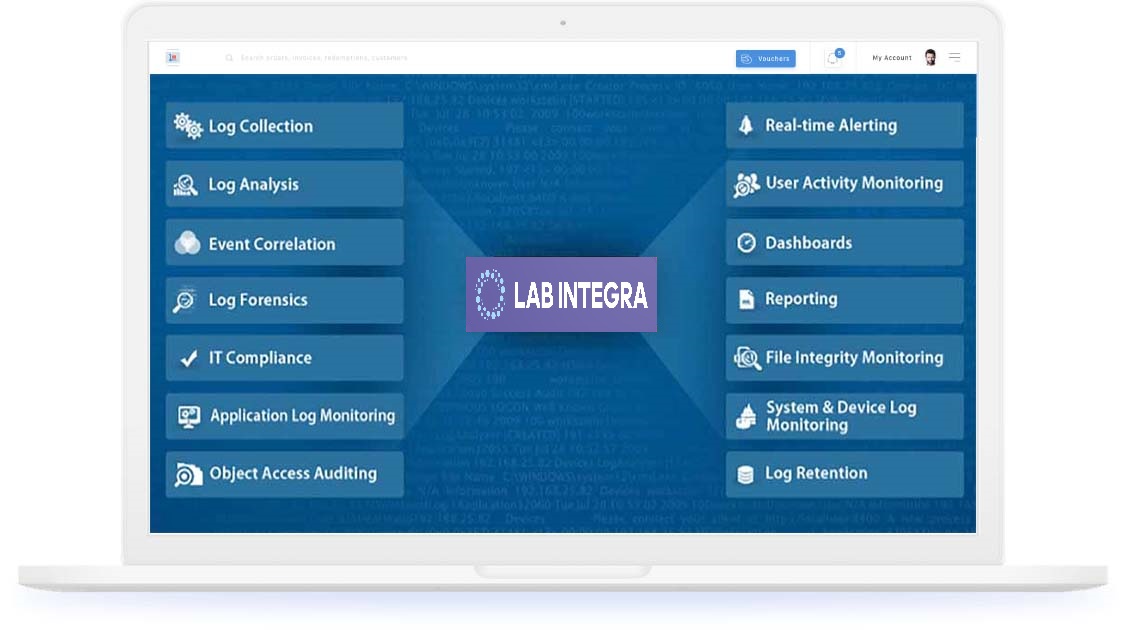
Our team has experience in the following

We follow a structured streamline workflow as per the needs and requirements of our customers.
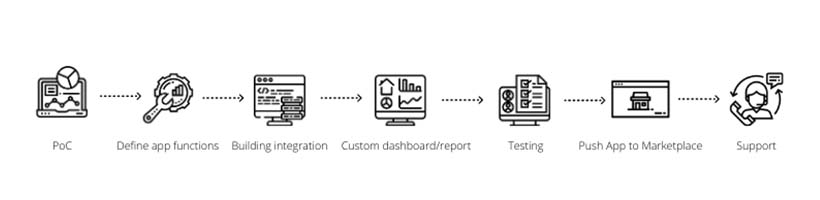


We did in-house security application development with Digital Shadows, QRadar, etc such as developed cybersecurity incident management processes for mitigating, removing, and preventing identified business risks. Also we automated change management procedures for comprehensive risk assessments and enhanced cyber hygiene and risk management by centralising and optimising firewall administration.
